What is ICS Security? Industrial Control Systems Cyber Security 101
ICS Systems refer to Industrial Control Systems that may be DCS, , PLC, SCADA or SIS systems, or a mix of these. Find out more about securing them from cyber threats in this Abhisam White Paper.

Understand Industrial Control Systems cyber security
Over the past few years there has been a growing interest in the subject of ICS Security. ICS stands for Industrial Control Systems. These systems are of various types such as DCS (Distributed Control Systems), SCADA (Supervisory Control and Data Acquisition Systems), PLCs (Programmable Logic Controllers) and SIS (Safety Instrumented Systems). They may be also a hybrid mix of older technologies such as single loop controllers & penumatic or electro-hydraulic systems. Sometimes ICS security is also referred to as SCADA Security or Industrial Control System security.
All of these systems are used to monitor and control processes in all kinds of industries and sectors such as oil & gas platforms, mines, oil refineries, steel plants, chemical plants, power generation plants, manufacturing plants, paper mills, electrical grids, water supply networks and many more areas. Many of these systems are legacy systems that are decades old and vulnerable to cyber attacks from various entities.Note that only programmable, computer based systems are vulnerable to these attacks. Older technologies like single loop controllers and pneumatic or electro hydraulic systems are not vulnerable.
This free Abhisam white paper on ICS Security provides a brief introduction to the subject. Fore information please refer to the Abhisam Cybersecurity collection.
What are Industrial Control Systems?
Industrial Control Systems refer to a broad class of systems that measure & monitor parameters, control and/or automate processes in a wide range of industries and sectors. Many of these systems are legacy systems that have been designed and built during a time when cybersecurity threats were almost non existent.
Legacy ICS Security
In earlier days, the only way to attack or sabotage these systems would be for a perpetrator, to physically access them and damage them with something like a hammer!
This is because generally, these systems are typically located in Control Rooms that have very good perimeter security and restricted access. These systems consist of either analog or digital hardware input cards, processors that run proprietary embedded software and communications utilizing various kinds of proprietary or standards based buses.
(Note: Read the Abhisam Industrial Cybersecurity myths whitepaper here)
Typically these legacy systems have Operator and Engineering stations (basically computer terminals) that have some kind of modern operating system based on some flavor of UNIX or Windows (not necessarily the latest version, you can find many that still run on obsolete versions like Windows CE and Windows XP). The operations personnel (such as manufacturing plant operators) control and monitor the plant (or offshore platform/building/ship-whichever is the equipment under control) via these stations. Engineering stations are used to configure the controllers, graphics displays, historical trend displays, etc. The Operator stations are from where you can Start/Stop pumps, open/close valves and monitor and control other stuff. Here is what a typical Control Room DCS Operator station looks like.

ICS Architecture, Security and Threats
As already explained above, the system architecture consists of lower levels of electronic hardware that comprises signal conditioners, amplifiers, galvanic isolators and so on that gather analog and digital signals coming from the plant, send it via DCS controllers to the operator stations, where they are displayed in the form of graphical user screens. The commands from the operator stations likewise travel from the operator stations, via the DCS controllers and so on until it operates a valve or a pump. Some operations are done manually while others may be done via control logic that uses the PID (Proportional Integral Derivative) or similar algorithms to sense changes in parameters and automatically adjust the outputs, so that the parameter remains near the desired value (called the set-point). This is shown in the picture below.
Note that these systems did not consider ICS security at all, when they were designed.
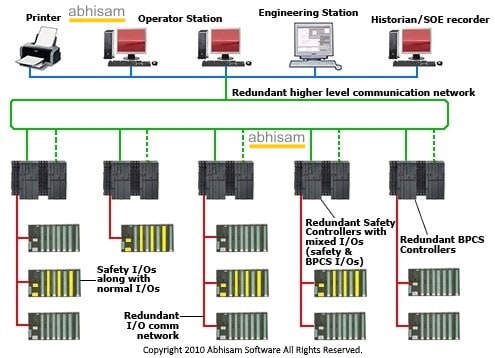
These systems face threats from a variety of adversaries including plain cyber criminals, ransomware seekers, bitcoin miners, bot herders as well as state and non state actors that wish to damage a country’s critical infrastructure, since many of these systems are also used in water supply, sewerage management, running the electricity grid.
How did we land in this poor security situation ?
At the time that many of these systems were designed and built, the personal computer was a novelty, available in only a few homes and the internet was just beginning to become popular. Over the next two decades there were several developments. The internet became commonplace, as did computers, laptops and mobile phones that were connected to the internet. Likewise, business IT systems also became modern. They moved from old mainframes running COBOL and DB2 to newer systems like SAP and Oracle based systems. The management of many of these manufacturing companies saw value in connecting these business IT systems with the older legacy control systems. Many of the business IT systems had web interfaces. However, either the managers were not informed properly, or did not budget for security of the older Control Systems. Now suddenly legacy ICS were connected to the internet and thus became vulnerable. But it was not just about systems that were directly connected to the internet.
Even those ICS that were modernized, were done so in a very superficial way. To save on upgrade costs, only the operator and engineering terminals were “upgraded” or “migrated” to better looking systems, with plant graphic displays and trends having thousands of different colors, the ability to use pointing devices like mice and the ease of having USB ports and CD and DVD drives for software backup.
Compromised Security
This however became the Achilles heel of these systems, because now malware could enter the system via these means and there was no mechanism that could detect and remove it. There have been several cases where such malware entered the ICS via uncontrolled use of USB drives, quickly leading to panic situations like blank screens, slow actions and so on, that had to lead to shutdown of the plant, associated downtime and what is worse, emergency situations where the plant had to be shut down.
These upgrades in fact, increased the attack surface of these systems because now malware could also enter the ICS via insecure serial connections, misconfigured firewalls and so on. Sometimes, the IT staff employed to maintain these systems had no idea of how fragile these Industrial Control systems really were (having little RAM and storage, not much processing power either, as compared to business IT systems) and discovered it the hard way after having inadvertently shutting them down while working on them.
Meanwhile the news that these systems were old and prone to being attacked got through the bad guys and they could now find these systems (many had insecure internet connections that could be breached). This led to many more attacks on these systems.
ICS Cyber security training & protection of these systems
Here’s an easy way to learn all about Industrial Cybersecurity and qualify as a Certified Industrial Cybersecurity Professional (CICP) at a fraction of the cost that is charged by other training providers. Click the image below to know how.
Understanding this via the Abhisam CICP course is the first step to protecting your Industrial Control System from cyber threats.
Why has cyber security for ICS become critical now? Can we do technology upgrades?
There are thousands of these legacy DCS, SCADA and SIS systems that are prone to being attacked from various entities such as general cybercriminals, cryptocurrency miners, hacker-activists (called hacktivists), various terrorist groups and even rogue states. These ICS security threats are real and several attacks have already taken place in the recent past, though you may not have heard of many of these, since they were not publicly reported. Since it will be an enormous task to replace this old insecure automation architecture, with a completely new one (such as an Industrial Internet of Things based one) is next to impossible, it has become critical to understand ICS security, carry out a risk assessment of these systems and protect them. To do this we need a proper ICS security framework and ICS security best practices.
Which organizations are responsible for ICS Cyber Security?
Primarily the asset owner is responsible to secure their systems from attacks, since they own the Industrial Control System as well as the plant and equipment that the ICS controls. However, in order to do this, in addition to utilizing their own resources such as their Instrumentation & Control Systems engineers (who also have been trained in ICS cyber security via a program such as the CICP), they may also need to take the help of other professionals such as ICS vendors and system integrators and OT cyber security auditors.
What is the Certified Industrial Cybersecurity Professional program?
This is the only budget friendly training and certification program that covers everything about ICS Security.
When you take the Abhisam Industrial Cybersecurity training course, you can earn a competency certificate and badge, as well as the CICP designation. 
You can also take our help in carrying out a cyber risk assessment of your facility and then take steps, based on our recommendations to secure it.
Do contact us to know more.
Standards and Regulations for ICS Security
There are a variety of different standards and regulations regarding ICS Security, that have to be followed, depending on the jurisdiction where the Industrial Control System is located and the industry in which it operates. Currently the following are commonly applied ICS Security Standards and Practices
- IEC 62443
This is a multi part standard developed jointly by ISA (International Society for Automation) and IEC (International Electrotechnical Commission). It is known as ANSI/ISA/IEC 62443 and as of now it contains 15 parts, but not all parts have been published yet. You can refer to this IEC 62443 guide to know more. - NIST 800-82 Rev 3
This is published by the US National Institute of Standards and Technology. More details here - NERC CIP
The North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) standards set mandatory cyber security requirements for the electricity sector in North America.
You can learn in detail about IEC 62443 in detail when you take the Abhisam CICP course. The Professional version also includes a detailed part on IEC 62443-2-4 compliance, which is important for Industrial Control System vendors and their system integrators to comply.



