Industrial facilities such as Oil & Gas rigs, Chemical Process Plants, Power generation plants (including Nuclear, Thermal, Hydroelectric), discrete parts manufacturing plants, electrical distribution grids, water and waste water facilities are all highly vulnerable to cyber attacks.
Carrying out periodic ICS Cyber Risk Assessment is essential for these facilities.
Why has ICS Cyber Risk Assessment become important today?
In the past few years cybersecurity has become an important part of securing them, in addition to normal physical perimeter security.
This may be shocking to those who are not from the Instrumentation, Control and Automation field.
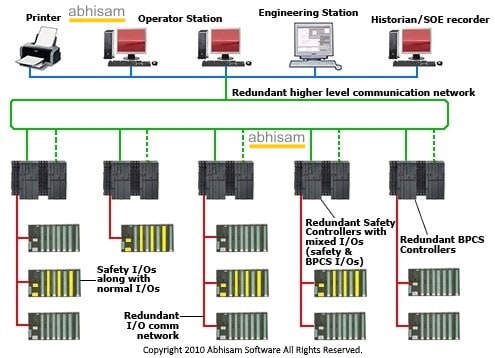
The sad truth is that most of today’s plant control and automation systems follow an older era of design where there was no internet, no USB drives, no connection with any business systems and therefore no possibility of these being attacked maliciously by cyber attacks. In olden times, the only way to damage a control system was to gain physical access to it, now it is not mandatory. Even today, in many facilities there is little to no control on who can access the control system.
The architecture of today’s control systems thus leaves much to be desired from a cyber security point of view.
Unlike a banking system or a stock exchange, attackers of Industrial Control Systems, are not interested in manipulating accounts or siphoning off money, rather they may be interested in causing disasters by manipulating the DCS, PLC or SCADA to behave in such a way that an undesired event can occur. This can result in asset damage (physical damage to plant and machinery) or cause loss of containment thereby triggering an environmental disaster or a gas discharge that can cause human injuries even outside the plant perimeter.
So you need to protect your ICS from these kinds of threats and the first step is to carry out a ICS Cyber Security Risk Assessment of your existing systems.
In fact the step before the first step (lets say Step 0) is to learn about this topic in depth, which you can do by taking our Industrial Cybersecurity course
Can an IT Cybersecurity professional carry out these risk assessments?
The answer is “It depends”. If the IT security professional is trained in Industrial Cybersecurity, knows about relevant standards such as IEC 62443 series, then they can do it. For example, many professionals who have undergone the Abhisam Industrial Cybersecurity training course can probably do it, if they have prior experience of carrying out IT security audits.
On the other hand, many generic cyber risk assessment consultants are basically Information Technology specialists, very good in business IT systems such as MIS or SAP (an ERP system) but may not completely understand the world of Industrial Control Systems (DCS, PLC, SCADA, SIS) , having never worked with them as a user or programmer or a system integrator or a developer.
Also they may have no idea about how industrial processes are controlled in the first place.
ICS security is a different animal from security of an ERP system like SAP or a business CRM system.
Unlike this situation, we at Abhisam have core specialization in Instrumentation, Process Automation and Control, coupled with Process safety, Functional Safety, plant operations and maintenance, design and installation/commissioning or large process plants. So we are in a much better position to evaluate the risks from your view point and can suggest and recommend measures that may not be thought of by IT specialists.
We can help you in carrying out an integrated Risk Assessment that also includes malicious attacks. Your normal HAZOP or LOPA will not cover this. Since this is a complex subject with many implications and moving parts, merely following a standard like IEC 62443 is not going to be enough. You may have to take guidance from a bunch of other standards and documents, to come up with your own plan.
We can help you in doing this.
Call us or email us today to know more.
Related Courses and White Papers
Industrial Cybersecurity Course

Learn all about Industrial Cyber security in this easy self paced e-learning course from Abhisam. To know about the current state of Industrial Cyber security in various industries such as Oil & Gas, Automation, Chemicals, Water and others, you can download the Industrial Cyber security report now..
Covers everything that you need to know about ICS security. Spread over several modules, it covers basic concepts about Industrial Automation and Control Systems such as DCS, PLC, SCADA , SIS, cybersecurity fundamentals such as authentication, encryption, assymetric keys, firewalls. It also covers standards like IEC 62443, the MITRE ATT&CK for ICS Matrix, Honeypots, finding vulnerable systems with SHODAN and more.
Contact Us by filling the form below OR call us OR email