If you have been working in the field of Industrial Control Systems cyber security (ICS security) or in the broader Operational Technology cybersecurity domain (OT security) then you may have heard of the standard ANSI/ISA/IEC 62443, referred to these days as simply IEC 62443. This standard has certain Foundational Requirements that are important and these are explained in short here.
This short guide will explain these IEC 62443 Foundational Requirements, but to really understand Industrial Cybersecurity in detail and also get certified as an Industrial Cybersecurity Professional, please take the Abhisam CICP Course now. (Click the image below to learn more about it). This is the most cost effective way, to learn all that you need to know about Industrial Cybersecurity and to get certified as a Professional, but at a fraction of the cost that you would otherwise spend on multiple other certifications from other providers.
First the basics.
What is IEC 62443?
The ANSI/ISA/IEC 62443 set of standards and practices is a joint effort by the ISA 99 committee. This ISA committee worked hard for many years on Industrial Cybersecurity to have a comprehensive standard that could provide guidance and direction regarding ICS security to a wide set of stakeholders such as asset owners/operators, IACS (Industrial Automation and Control System) vendors, system integrators, design engineering consultants, EPC companies that build manufacturing plants and others.
Note that the term IACS includes not only Industrial Automation and Control Systems (that may themselves be based on DCS – Distributed Control Systems or PLC – Programmable Logic Controllers, or other kinds of electronic controllers), but also other operational technology systems such as Safety Instrumented Systems, Building Automation Systems, SCADA (Supervisory Control and Data Acquisition systems) as well as specialized systems such as HIPPS (High Integrity Pressure Protection Systems) and BMS (Burner Management Systems). Hence we use the term IACS, it could be any or all of these systems.
This ground work resulted in a planned set of standards that dealt with Industrial Control System cybersecurity, whether based on DCS, PLC, SCADA or other technologies and architectures, whether used as BPCS (Basic Process Control Systems) or SIS (Safety Instrumented Systems) or as Building Automation systems. Note that collectively these systems fall under the category of OT (Operational Technology) systems.
ISA later on collaborated with IEC (International Electrotechnical Commission) for a common set of standards, that could be used globally (not just in the US) and these efforts resulted in the series now referred to as ANSI/ISA/IEC 61443 series of standards. Many parts of this series have been published by ISA and some parts by IEC. However, all parts whether published originally by ISA or IEC, are now included in the series and referred to as ANSI/ISA/IEC 62443 or simply as IEC 62443 or even just as “62443 standard series”
IEC 62443 parts
As of now, there are about 14 parts in the IEC 62443 series, although some more are being planned. Note that even among the 14 parts, not all have been published and some are still in the draft / planning stage. All the parts are shown in the chart below. This is also referred to as the ISA IEC 62443 framework.
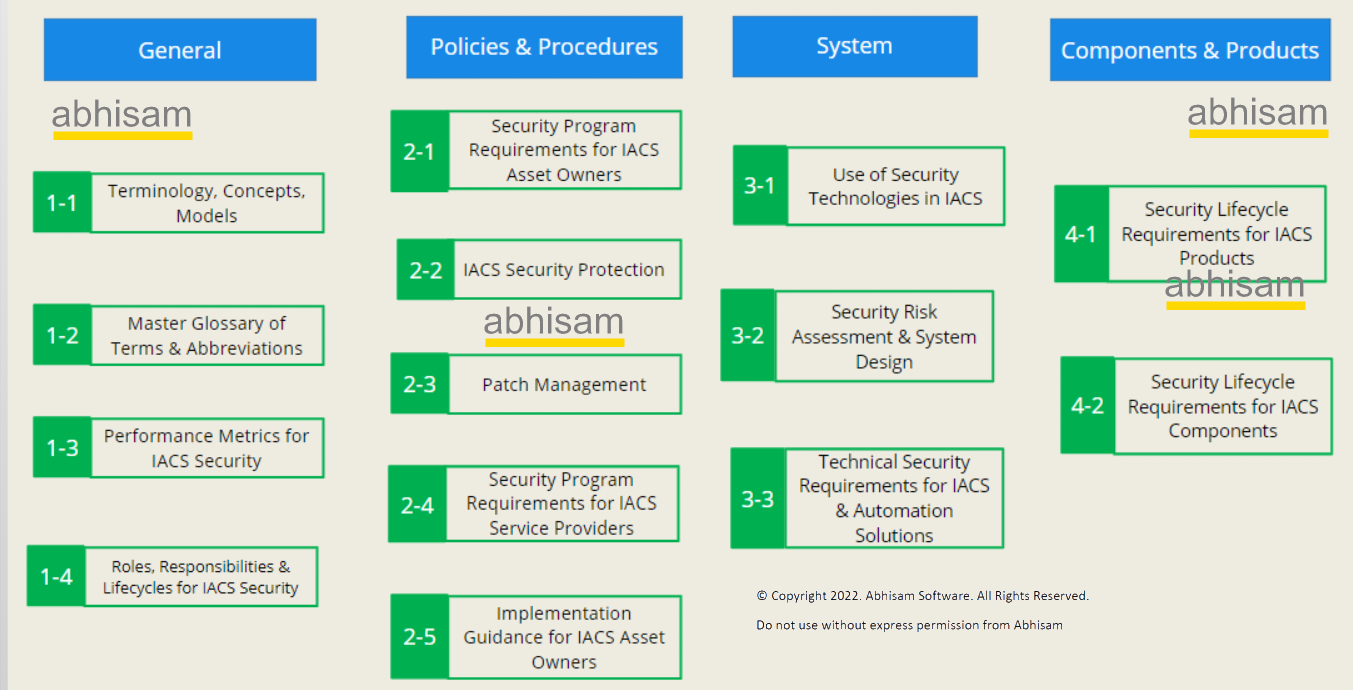
There is no single IEC 62443 standard pdf available. Each part is a separate pdf that has to be purchased from the IEC website or from authorized standards distributors. However, ISA members can view the parts that are published by ISA for free on their website in the member’s area. But the parts that are developed and published by IEC themselves (such as for example IEC 62443-2-4), are not available for viewing in the ISA member area and have to be purchased separately from IEC.
IEC 62443-1-1
This is the first part of the IEC 62443 series and the one where the Foundational Requirements are introduced. These Foundational Requirements (FR for short) are then referenced throughout the IEC 62443 series, so it is essential to understand them. There are seven FRs and they are listed below in the table.
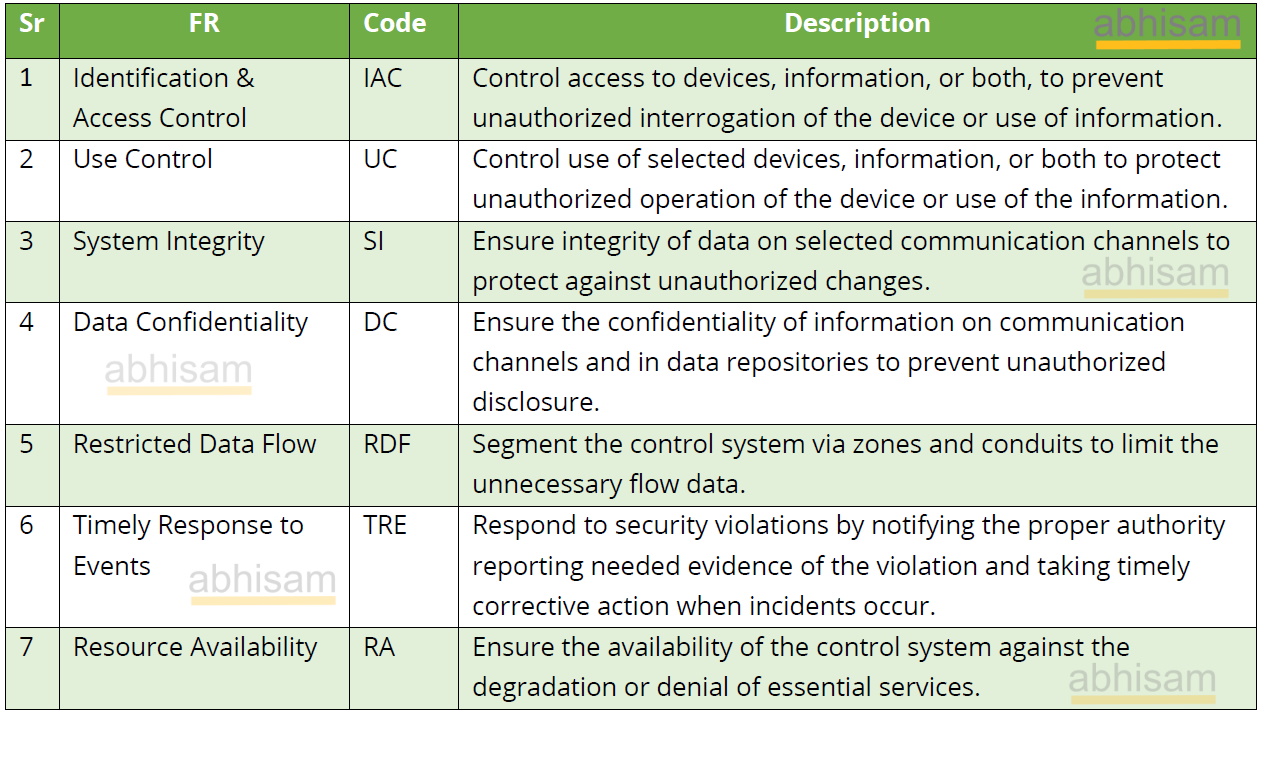
IEC 62443 Foundational Requirements Explained
Identification & Access Control (IAC)
This ensures that the devices as well as the information that they possess can only be accessed by genuine entities, having the necessary permissions, who need this access, in order for the plant or facility to be operated safely, and in a manner in which the IACS is designed to operate it.
Use Control
Use Control (UC) ensures that only authorized entities can use the devices and/or the information that they possess for valid and necessary tasks that are essential to maintain the safety and productivity of the plant or facility. The principle of “least privilege” is to be followed.
System Integrity (SI)
This Foundational requirement ensures that there cannot be any unauthorized changes to data in the communication channels, so that only genuine and correct data is available. For example, the process values that are displayed on a DCS operator’s screen must be the real ones and not manipulated by malicious entities, as happened during the Stuxnet attack.
Data Confidentiality (DC)
All data in the IACS should remain confidential and should not be accessible to outsiders or unauthorized insiders, whether malicious or not.
Restricted Data Flow
This Foundational Requirement ensures that every entity gets the information only on a “need to know basis”. Thus there should not be unnecessary data flows to areas where it is not required. For example, there may not be a valid reason to send any data from an Enterprise level ERP server to the SIS logic solver of a plant. This implies that the system architecture as well as the hardware and software configuration should be carefully designed, so that the system can be partitioned properly into Zones and Conduits, with appropriate security levels. The use of devices such as a Unidirectional Gateway and Data Diode, or similar can help.
Timely Response to Events
This Foundational Requirement of IEC 62443 ensures that the IACS shall provide the necessary capabilities, to respond to security violations by notifying the proper authority, reporting evidence of the violation and taking timely corrective action upon discovery of such an incident.
Resource Availability
Ensure that the design and operation of the IACS is such that there are no “denial or service” situations, where the IACS cannot operate the plant or bring it to a safe state. In any situation the Safety Related System, such as the Safety Instrumented System should not be prevented from shutting down the plant or bringing it to a safe state, even under a Denial of Service Attack.
These Foundational Requirements are referenced all through the different parts of the IEC 62443 series. The different parts of the IEC 62443 series have guidance on how to meet these FRs while implementing the parts.
IEC 62443 parts- what you need to know
Note that all parts of IEC 62443 have not been published as of now, so you can only refer to the ones that have been published. This standard is useful for not only IT Security auditors who may need to audit IACS or other OT systems as part of their job, but also for Instrumentation, Control Systems, Automation engineers who design, build, integrate and maintain these systems including those engineers and technicians who work for Asset Owners (such as Oil & Gas companies, chemical manufacturing plants, or Water utilities as typical examples), but also IACS vendors and their system integrators, as well as EPC companies that design and build plants and facilities.
What is the Understanding IEC 62443-2-4 course?
This course focuses on thoroughly understanding IEC 62443-2-4 part of the IEC 62443 standard. This part is meant for Industrial Automation and Control systems vendors, their system integrators and other Operational Technology vendors and system integrators, who provide automation solutions to asset owners/operators. It is also useful for asset owners/operators to know what to expect (and whether the vendor or system integrator is delivering as expected) a solution that is supposed to be secure.

You can take this as an individual course, or better still access it as a part of the Professional version of the Abhisam Industrial Cybersecurity course (CICP course), when you take the CICP course.
The Abhisam Industrial Cybersecurity Course gives a great explanation of all the IEC 62443 parts.




