For those new to OT Cyber security, here is a brief guide.
A Brief Introduction to OT Cybersecurity
This guide will help you quickly understand Operational Technology cyber security (OT Cyber Security) if you are new to it. After reading this, you can read other articles related to OT Cybersecurity on this site. You can also take the OT Cybersecurity Awareness course, as well as other courses such as the Certified Industrial Cybersecurity Professional course to qualify as a professional.
What is Cybersecurity?
Cybersecurity has varying definitions. For example, Microsoft says “Cybersecurity, also known as digital security, is the practice of protecting your digital information, devices, and assets.”
Gartner, a big consultancy organization says ”Cybersecurity is the practice of deploying people, policies, processes, and technologies to protect organizations, their critical systems and sensitive information from digital attacks”.
Abhisam’s definition is a little different. According to Abhisam, “Cybersecurity is all about protecting Digital Information as well as physical assets from a digital attack, that may result in theft or misuse of information, or damage of assets and consequential damages to assets, people & the environment”.
This is because Cybersecurity is not only about protecting data, money or digital information, it is also about protecting physical assets from damage.
It may be sound surprising to many, that a cyber attack can lead to damage of physical equipment and physical consequences. This is because in the modern world, a lot many industrial plants, facilities and equipment are controlled by computer based systems. These are referred to as OT Systems, where OT stands for Operational Technology.
What are OT Systems? How are they different from IT Systems?
Most people are familiar with IT (Information Technology) systems. Typical IT Systems include, but are not limited to online Banking Systems, ERP systems like SAP, Stock Market trading systems or online Hotel Reservation systems. These systems process only data.

On the other hand, OT Systems are cyber physical systems. These systems process data as well as monitor and control physical objects in the real world. Examples include Industrial Automation and Control Systems, Ship Steering Systems, Port Cranes and Warehouse Robotic Automation systems.
Other examples of OT Systems are Industrial Robotic systems, Medical/Surgical Robotic systems used in Healthcare and Transportation Control Systems (such as train control systems) and Military Systems such as Artillery Fire Control Systems.
Why is OT Cybersecurity important?
A cyber attack on an IT System may result in loss of data, theft of data and loss of money. However, it does not result in physical injuries or harm to the environment. But a cyber attack on an OT System may result in not just loss of data and theft of data, but may also result in physical damage to equipment as well as damage to the environment as well as a national emergency if the system is part of Critical Infrastructure of a country.
Note: Industrial Cybersecurity is a subset of OT cybersecurity. But for most purposes, they are synonyms and can be used interchangeably.
Do OT Systems get attacked? Has it resulted in physical harm?
OT Systems do get attacked all the time, but not as frequently as IT Systems. OT system attacks can result in various kinds of damage, including consequential damages. For example, in the Stuxnet attack, Iran’s Uranium Processing plant was cyber attacked resulting in damage to hundreds of centrifuges, pushing back their nuclear program by several years.
There have been several attacks on the Ukrainian power grid by suspected Russian attackers, leading to not only widespread electrical supply failures, but also damage to circuit breakers and suspected transformer fires.
A cyber-attack on the OT System (SCADA) of Colonial Pipelines in the US, caused widespread shortages of gasoline on the US East Coast, although no physical damage was reported. There have been attacks on water supply utilities in the US, such as the one in Oldsmar, FL where attackers attempted to poison the water supply by increasing the injection of water treatment chemicals (but were thwarted due to alert employees).
There have been more than 50 reported attacks on OT Systems in the past one year, which may not seem like many, but the numbers are growing and not all attacks are reported. Also note that victims rarely post details about these attacks and the authorities are also not keen to publicize them for various reasons.
A few attacks have been listed here.
Table 1: List of OT cyber attacks (partial)
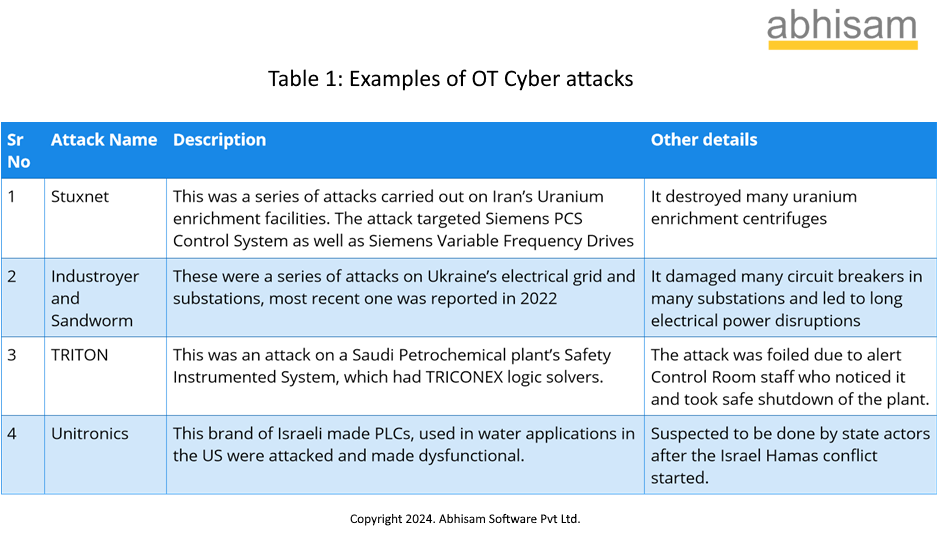
Note that the above list is a small fraction of actual attacks that have taken place on OT Systems.
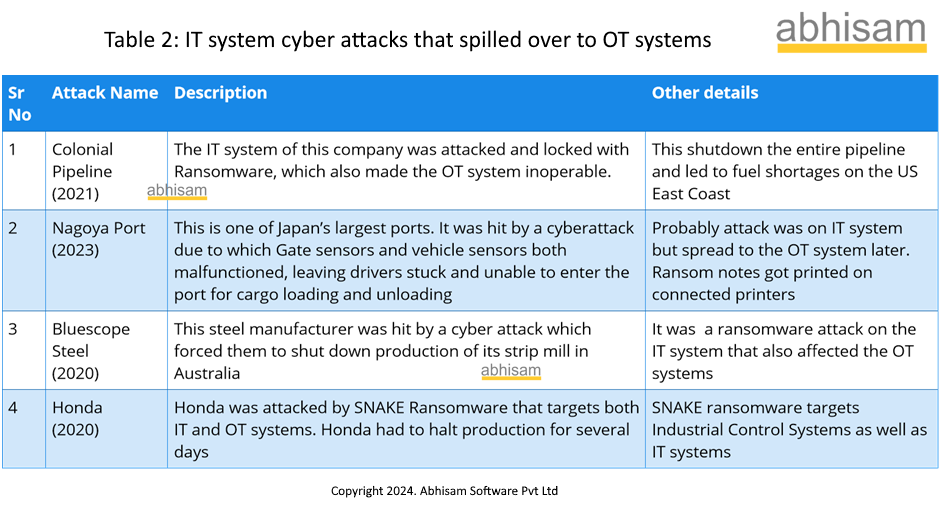
Sometimes, IT systems of organizations get attacked and the attack then spills over to OT Systems. The following is again a small sample of such attacks that have taken place in the past.
Table 2: List of IT cyber attacks that spilled over into OT systems (partial)
Why are OT Systems vulnerable to cyber-attacks? How can we protect them?
Most OT Systems are legacy systems and were designed and built with no cybersecurity, because this was not a big problem at that time. Secondly, due to various reasons, many organizations have connected these systems to their IT Systems, but without adequate protections. Thirdly ignorance about OT cyber security is a big problem. Fourthly, the use of IIoT devices (Industrial Internet of Things devices) in Industrial OT Systems have complicated matters more. Lastly OT cyber security is difficult because almost every OT system is a unique solution that is custom built for the application. No two OT Systems are exactly the same when they get installed on premises of an asset owner (such as an oil refinery or a warehouse). Hence OT cyber security solutions also are unique and there is no one size fits all kind of answer.
However, OT systems are not only attacked via their internet connections- but they can also be attacked in other ways too. So mere disconnection from the internet is not sufficient.
The first step in protecting OT Systems is to be aware about OT Cybersecurity. Abhisam has an OT Cybersecurity awareness course that can be taken by employees of organizations that have OT Systems.
Abhisam has also developed the Certified Industrial Cybersecurity Professional program (CICP®) that helps professionals acquire knowledge and skills in OT cybersecurity.

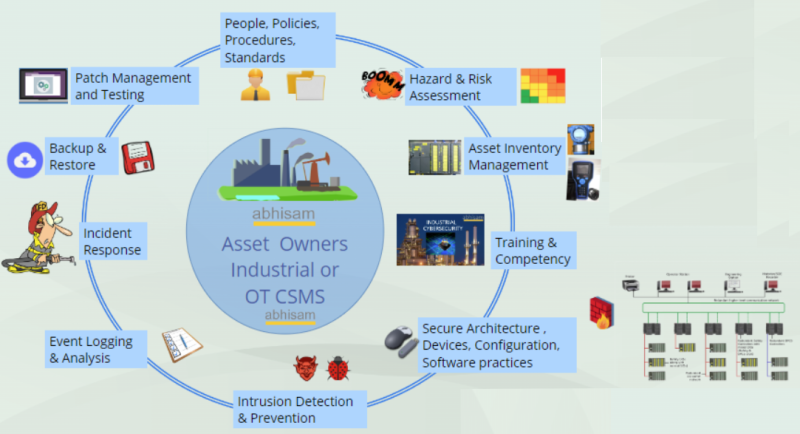
Further steps include evaluating the current security posture of your OT Systems by carrying out an OT Security audit, modifying your system architecture, carrying out an OT cyber security assessment, an OT cyber risk assessment, developing a robust Cyber Security Management System (CSMS), taking guidance from standards such as IEC 62443 and NIST 800-82 and following the Abhisam OT Cybersecurity Lifecycle controls.
(Please see image below. Click it to see an interactive version).
All this is covered in the Abhisam CICP course.
For more information, please visit https://www.abhisam.com/cybersecurity-information/ or contact us at sales@abhisam.com