In this short guide, we will take a look at what we mean by ICS security assessment. ICS is short for industrial Control Systems. These may be DCS (Distributed Control Systems), or PLC (Programmable Logic Controllers) based, or some form of SCADA (Supervisory Control and Data Acquisition Systems) or any other programmable type systems. These include not only BPCS (Basic Process Control Systems) but also SIS (Safety Instrumented Systems).
These systems are used to monitor and control plants and facilities and also to ensure that they can be safely shut down in case of trouble. These are critical systems. Hence, ICS cybersecurity Risk assessment should be an important part of your industrial cyber risk management strategy.
To learn more about ICS Cybersecurity, please consider joining the Certified Industrial Cybersecurity Professional (CICP) training program.
ICS Cybersecurity Risk Assessment
Many industrial facilities such as chemical process industries, oil and gas production platforms, petroleum refineries, steel plants, pharmaceutical plants, power generation plants, discrete parts manufacturing plants and similar industrial facilities all make use of Industrial Automation and Control Systems (IACS for short). These systems also include Safety Shutdown systems such as Safety Instrumented Systems (SIS for short). All modern plants use them and in fact it is not possible to run today’s large facilities, without using some form of automation, hence the dependence on these systems has only increased in the past few years.
For Convenience, we refer to all of them as simply ICS.
A major part of these systems employ programmable computer based systems that are vulnerable to cyberattacks. This is not fear mongering, there have been many actual cases of these kinds of attacks on industrial systems. Not all of these may be targeted specifically for ICS, but quite a few are. Recently, the entire motorcycle production at Suzuki plants in India got shut down due to a cyber attack and caused loss of production of tens of thousands of motorcycles.
In this case, the loss was only monetary, as a motorcycle manufacturing plant does not involve storing or processing large amounts of hazardous and toxic chemicals, like an oil refinery or a chemicals manufacturing plant. What if a similar attack happened on a plant that stores or handles large amounts of flammable, explosive and/or toxic materials. Loss of control of the ICS may result in fires, explosions, loss of containment, asset damage, and injuries to people along with severe environmental damage, in addition to monetary loss.
In such cases, a comprehensive cyber risk assessment needs to be carried out. Normally a cyber risk assessment of only IT systems is done, to assess how vulnerable the IT system is to cyber attacks and whether such attacks would result in loss of data, loss of confidentiality and loss of money. But in case of ICS, this risk assessment should also cover physical consequences that can result due to a cyber attack. These are as stated above fires, explosions, toxic gas releases, asset damage, injuries and environmental damage.
Thus ICS cybersecurity risk assessment is different from other IT cybersecurity risk assessments.
How to carry out an ICS Cybersecurity Risk Assessment?
This would have several steps. First of all it is useful for the organization to follow a standard such as IEC 62443 or NIST 800-82, when thinking about ICS cybersecurity risk assessment. This is because these standards are widely accepted in the industry and cover a lot of ground. By following any one (or both) of these standards, one can safely assume that almost everything would be covered.
Note: the current NIST 800-82 Rev 2 is due for replacement with NIST 800-82 Rev 3 which is currently in draft status but should be approved soon.
What does OT cybersecurity mean?
OT systems refer to Operational Technology and are cyber physical systems, as against IT systems, which are pure data processing systems. All ICS are OT systems. Hence OT cybersecurity risk assessment is the same as ICS cybersecurity risk assessment. Abhisam conducts OT cybersecurity training from time to time.
How are IT cyber risk assessments different from OT cyber risk assessments?
For process plants and those facilities that process hazardous or toxic or flammable and explosive materials, or radioactive materials, the conventional IT cyber risk assessment studies may not be enough and have to be combined with cyber PHA to determine the total risk. This is because in case of a cyber attack on an IT system, the consequences would be loss of confidentiality, loss of data, loss of integrity of the data and monetary loss in case the system is connected with banking, finance, payment systems or other financial systems.
However there are no physical consequences.
In contrast, a cyber attack on an OT system (which is what an ICS is) can result in physical consequences, such as damage or destruction of assets, fires, explosions, toxic releases, loss of containment, injuries to people, damage to environment and so on.
Using IEC 62443 for risk assessment
As you probably know by now, IEC 62443 has several parts. You can find an short IEC 62443 guide here. Of all these parts, IEC 62443-3-2 is the part that deals with security Risk assessment for system design. It mainly focuses on the ICS system architecture, and has various Zone and Conduit Requirements.
The included flowchart recommends that existing PHA studies be used as inputs to determine the existing risk of the facility.
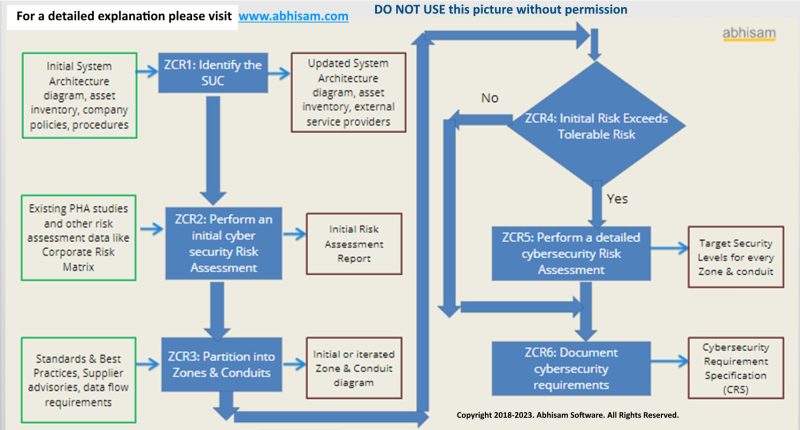
Here is where cyber PHA comes in.
What is a Cyber PHA?
PHA as you probably know, stands for Process Hazard Analysis and is a basic requirement while designing a plant that will store or process hazardous materials and where the risk of having a toxic release or fire, explosion, asset damage or other bad consequences is high. The PHA study enables the asset owner to incorporate several mechanical, electrical, electronic and operational safeguards to either prevent dangerous conditions from occurring at all or in case one of them occurs, by having mitigations in place. These are countermeasures.
PHA Studies are carried out using techniques such as HAZOP (Hazard and Operability Study), What-If analysis (also referred to as SWIFT which stands for Structured What-If Analysis). They may also include deeper studies like LOPA (Layer of Protection Analysis) for critical parts of the process.
Note: You can learn more about these techniques via various Abhisam courses.
Problems with currently used PHA techniques.
Many of these techniques in their current form, do not consider the possibility of electronic countermeasures failing due to a cyberattack. Thus, if the programmable Safety Instrumented System itself fails due to a cyber-attack, then the plant can have an undesired incident that may damage assets, environment, injure people and also result in huge monetary losses.
Hence, to evaluate these, we use Cyber PHA. Abhisam will soon have an online course on this. If you would like to take it, please contact us so that we can inform you once released.
Here is a small video that explains the process.

Where can I learn more about Industrial Cybersecurity?
You can browse around this site for the basics of Industrial Cyber Security and OT security. You can also take the popular Certified Industrial Cybersecurity Course (CICP) that covers this in great detail and helps you stand out from the crowd. This is because after yo complete the course, pass the exam and meet the eligibility requirements, you are awarded the designation of Certified Industrial Cybersecurity Professional (CICP). 
This includes a certificate and a digital badge that you can display on your LinkedIn profile. You can also append the title to your name, such as John Q Public, CICP.
Note: The Abhisam Logo and the CICP mark are protected marks in the US and multiple countries. They belong to Abhisam and cannot be used without permission.




