Update (13th June 2024): The IEC 62443-4-3 draft is now undergoing a ballot and will be renumbered as IEC 62443-1-6. This seems a bit unusual, as generally IEC does not change the number of the draft standard to a different one when it becomes a fully approved standard. We will post more information about this when we receive it. This means that now the Devices and Components section would have only two parts as earlier (instead of the proposed three) which are IEC 62443-4-1 and IEC 62443-4-2
This short guide gives you an introduction to the new IEC 62443-4-3 part of the IEC 62443 set of standards.
Note: To learn about Industrial Cybersecurity and IEC 62443, you can take the Abhisam Certified Industrial Cybersecurity Training Course here. This leads to certification as a CICP after you complete all the modules and pass the exam. It is better than just certifying oneself to only one part of the standard such as getting IEC 62443-2-4 certification (How to achieve IEC 62443-2-4 compliance, is included in the Abhisam CICP course).
Before jumping directly into IEC 62443-4-3, let us first understand more about IEC 62443. If you already know IEC 62443 and want to know directly only about this new addition, then you can skip and go directly to the part that describes IEC 62443-4-3 here.
What is IEC 62443?
IEC 62443 (officially ANSI/ISA/IEC 62443) is a set of Standards & Technical Reports that deal with Industrial Cybersecurity. The following picture gives an idea of the different parts of the standard. You can see that it is a multi-part standard. All parts have not been released yet, whereas some earliest parts, released more than a decade ago are undergoing revisions.
The set is divided into four groups and there are various documents under each category. IEC 62443-4-3 is still in draft mode and open for comments. Hence it has been shown in a Red Box in the below picture.
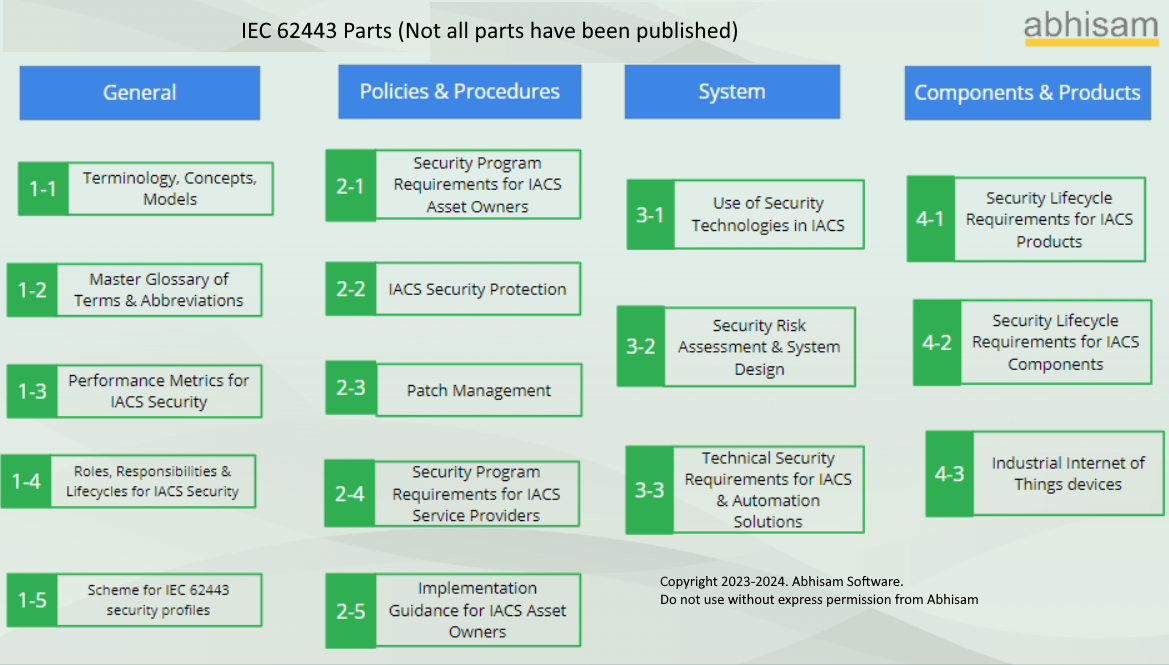
If you are new to Industrial Cybersecurity or OT security, you can read the next three sections below. Else you can skip directly to the section about IEC 62443-4-3.
Who is an Asset Owner?
An asset owner is the entity that owns and/or operates a plant (such as factory manufacturing widgets or an oil platform producing oil), or a piece of equipment (such as a Gas Turbine). Asset owners operate and control their plants and equipment using Industrial Automation and Control Systems, known as IACS in short.
What is an IACS?
IACS refers to Industrial Automation and Control Systems. IACS is a fairly broad term that covers the BPCS (Basic Process Control System) or SIS (Safety Instrumented System) or both.
The BPCS could be either one system like a DCS (Distributed Control System), PLC (Programmable Logic Controllers), HMI (Human Machine Interfaces), SCADA (Supervisory Data Acquisition or any combination thereof. It could also be a group of stand alone pneumatic or electronic single loop controllers. These monitor and control parameters based on various sensors, transmitters, actuators and final control elements which are popularly referred to as “field” devices because they are out in the field, as compared to the Control Systems, which are typically located in one or more buildings and control rooms.
Similarly the SIS could be either Hardwired systems or Programmable Electronic systems or Pneumatic or electromechanical systems or combinations of these. They may or may not use Programmable Logic Solvers. Sometimes they are specialized in doing only one kind of thing (such as Overpressure Control done by a HIPPS-High Integrity Pressure Protection System or a Burner Control system for a fired heater).
IACS is therefore what is referred to as OT (Operational Technology). These OT systems use computers to monitor and control physical stuff, such as manufacturing plants, as opposed to IT (Information Technology) which refers to computers that process data (such as those used in Banking systems or stock market trading).
What is OT security?
OT security is the domain of securing IACS from cyber attacks. Many times, OT security could be referred to by some people as IACS security, or ICS security or SCADA security or DCS security. All of these terms are more or less synonymous because the techniques used to secure a DCS (Distributed Control System) is not much different from that used to other systems such as a SCADA (Supervisory Control and Data Acquisition system). ICS is a generic term that stands for Industrial Control Systems. In Abhisam guides, e-learning courses and Instructor led workshops, we refer to these systems as IACS. These are also referred to popularly as cyber physical systems.
OT security is completely different from IT security because bad OT security can harm people physically, damage assets physically and spoil the environment due to an unwanted chemical release or oil spill.
On the other hand, bad IT security can only cause financial loss, not injuries or accidents.
What is IEC 62443-4-3?
IEC 62443-4-3 is the latest part of the standard and it deals with Industrial Internet of Things (IIoT). This section (iec 62443 4) deals with Components and Products. A component may be a smart transmitter or a PLC controller or a software package (such as Batch Historian).
Currently, IEC 62443-4 has two parts under it, IEC 62443-4-1 and IEC 62443-4-2. The first part IEC 62443-4-1 deals with the management aspects of developing secure components that can be used in Industrial systems. The second part IEC 62443-4-2 mainly deals with the technical aspects of developing secure components that can be used in Industrial Automation and Control Systems.
As you probably know IIoT is the Industrial avatar of the Internet of Things. The word “Industrial” is to distinguish it from the consumer oriented IoT devices that are currently available, such as home automation products. Unlike consumer IoT devices, Industrial IoT devices have to work in harsher environments and must be secure from the ground up, to ensure that they do not themselves compromise the security of the Industrial Automation and Control System (IACS) that they work in.
What is the purpose of IEC 62443?
IEC 62443 was devised to help asset owners protect their electronic programmable IACS from cyber threats. Many of these systems are legacy systems, designed well before cybersecurity became mainstream. IEC 62443 helps these systems (that are not designed to be secure from the ground up) to be protected and secure from cyber attacks on Industrial Systems.
Who is IEC 62443-4-3 for?
This document is aimed at asset owners and their service providers (such as IACS vendors, system integrators and EPC contractors), who would like to know how to securely use IIoT devices in their Industrial Control systems. In the last few years, IIoT technology has become almost mainstream and in the next few years these devices may become ubiquitous. Previously, the Purdue Enterprise Reference Architecture (PERA), popularly referred to as the Purdue Model was used as a reference model for IACS, however the assumptions in that model are today no longer true. In that model, the devices at Level 0 (the field level) were not as smart and had no connectivity directly to other outside systems. Today however a small temperature sensor can also be an IIoT device, that can connect to the Cloud directly, bypassing all higher levels of the PERA model. The PERA model was used to describe Functionality of existing IACS, but it began to be used as a model to implement a secured architecture, which was not originally envisaged.
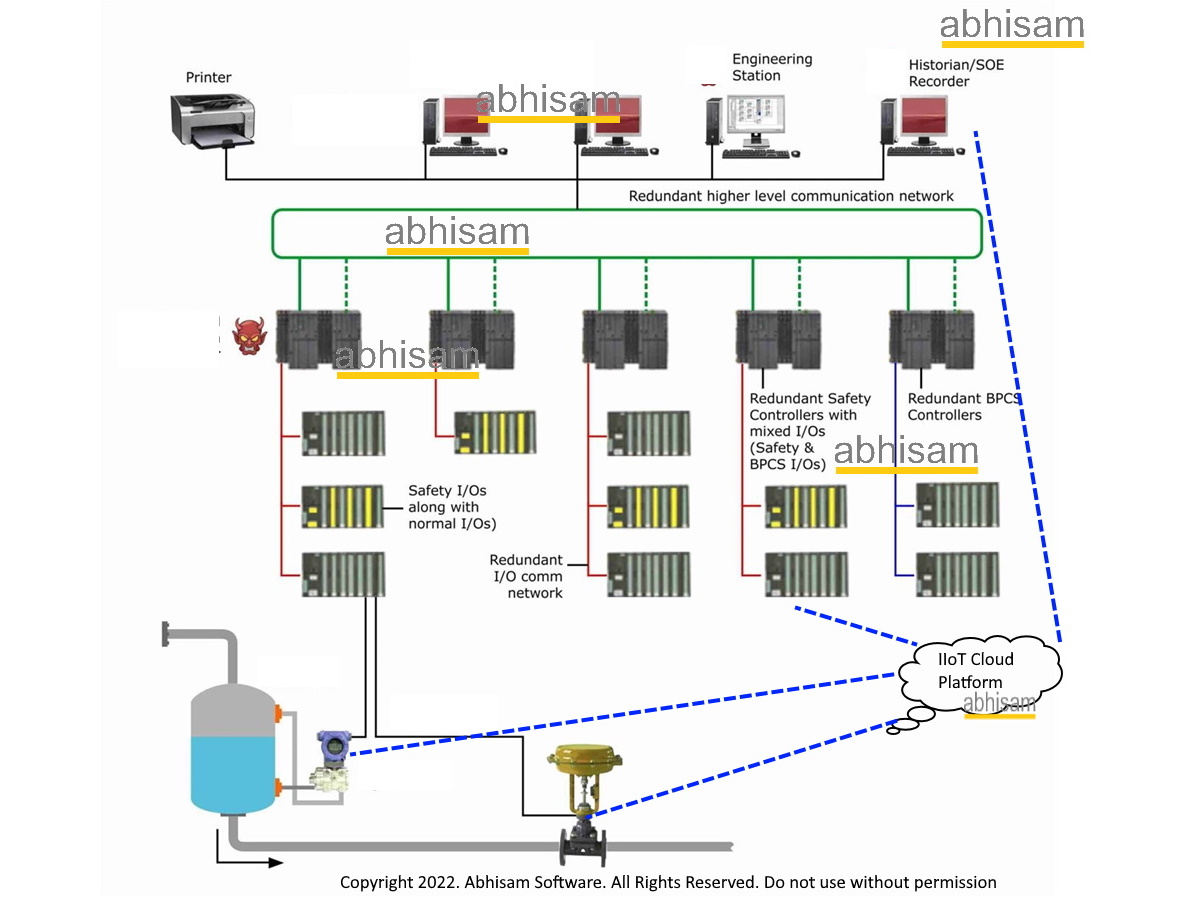
These developments were noticed by the ISA committees and work began on using IIoT devices, without hampering security. This draft Technical Report (TR) deals with various aspects of using IIoT devices in IACS.
The dotted blue lines represent possible direct communication channel to a cloud IIoT platform, whether in premise cloud or external.
Zero Trust Architectures
Zero Trust architecture is a newer model of ensuring security that does not depend solely on perimeter security. Instead every time a device has to access a resource, authentication and authorization have to be provided. Currently all devices that are part of a single Zone “trust” each other and the Zone boundaries are protected. However in an IIoT enabled device, this is challenging, so the use of Zero Trust is needed as the IIoT device may have the capability of establishing communication channels with other devices and the cloud in multiple ways and all of these cannot be bounded by a single perimeter that is secured.
What else is covered in IEC 62443-4-3?
IEC 62443-4-3 gives details of Zero Trust architectures. It also has information related to integrating IIoT technology into the Asset Owner’s Security program, using IEC 62443-2-1 and Risk Assessments of IIoT technology using IEC 62443-3-2. It also talks about considerations for integration of IIoT with cloud based functionality into IACS.
You can enroll in Industrial Cybersecurity training here



